
- Introduction to AWS WAF
- How AWS WAF Works
- Key Features of AWS WAF
- Use Cases of AWS WAF
- AWS WAF vs Traditional Firewalls
- Configuring AWS WAF Rules
- AWS WAF with AWS Shield and AWS Firewall Manager
- Logging and Monitoring with AWS WAF
- Security Benefits of AWS WAF
- AWS WAF Pricing Model
- Best Practices for AWS WAF Implementation
- Conclusion
Introduction to AWS WAF
Amazon Web Services (AWS) Web Application Firewall (WAF) is a security service that helps protect your web applications from common web exploits that could affect availability, compromise security, or consume excessive resources. AWS WAF is a flexible, cloud-native firewall that protects applications running on AWS resources, such as Amazon CloudFront, Application Load Balancer (ALB), and API Gateway. Amazon Web Services Training covers how the service allows you to set up custom rules to filter web traffic, helping to safeguard against malicious activity like SQL injection, cross-site scripting (XSS), and denial-of-service (DoS) attacks. AWS WAF is a scalable and cost-effective solution that provides businesses with the tools necessary to enhance security without managing infrastructure or dedicating resources to on-premises hardware.
How AWS WAF Works
AWS WAF operates by inspecting web traffic in real-time and applying rules that define the conditions under which the traffic will be allowed or blocked. It examines HTTP and HTTPS requests sent to your AWS-hosted applications, enabling it to detect patterns and behaviors characteristic of attacks. When you use AWS WAF, you create a web ACL (Access Control List) that defines a set of rules for your application. These rules can be custom or based on predefined sets of security controls that AWS provides. AWS WAF inspects incoming web traffic based on specified rules, and depending on the inspection, it either allows, blocks, or counts the traffic according to the rule set. If the traffic matches the criteria of a blocking rule, AWS WAF will deny access to the request. If it matches an allow rule, the request will be passed through, and if it’s part of a count rule, it will be logged for review, but the request will be allowed. The service integrates seamlessly with other AWS services, such as Amazon Cloudfront and It’s Benefits, ALB, and API Gateway, enabling it to filter traffic before it reaches your web application infrastructure. This integration ensures that web applications are protected from a wide variety of attacks while maintaining high performance and availability. AWS WAF also offers scalability, allowing you to automatically adjust security settings as traffic volume fluctuates. It provides real-time metrics and logging, making it easy to monitor security threats and take proactive action. With AWS WAF, you can achieve fine-grained control over web traffic to safeguard your applications efficiently.

Key Features of AWS WAF
AWS WAF offers several powerful features that help organizations secure their web applications:
- Customizable Rules: You can create custom security rules based on specific patterns or conditions you want to block or allow. These rules can inspect the request’s headers, body, URI, and query string.
- Predefined Managed Rules: AWS provides predefined rule sets through AWS Managed Rules, which include rules for common threats like SQL injection and XSS attacks. These rules are updated automatically to help defend against new and evolving threats.
- Real-time Protection: AWS WAF provides real-time monitoring and logging, allowing you to track the status of web requests, gain visibility into malicious activity, and adjust rules accordingly.
- Rate Limiting: AWS WAF, one of the Top AWS Services, can help prevent brute-force attacks by allowing you to set rate limits on the number of requests that are allowed from a specific IP address in a defined period. This can be particularly useful for defending against DoS or DDoS attacks.
- IP Set Management: AWS WAF supports using IP sets, which enable you to block or allow traffic from specific IP addresses or address ranges.
- Geo-Blocking: You can block traffic from specific geographic locations based on the request’s origin, helping to mitigate risks from high-risk regions.
- Bot Control: AWS WAF offers bot control features that help identify and mitigate automated traffic generated by malicious bots. Using CAPTCHA, you can set up rules to block traffic from known bad bots or challenge suspected bot traffic.
- Logging and Metrics: Integration with AWS CloudWatch allows you to monitor and log web traffic to gain insight into threats, detect anomalies, and trigger alerts for potential attacks.
Excited to Obtaining Your AWS Certificate? View The AWS Course Offered By ACTE Right Now!
Use Cases of AWS WAF
AWS WAF is suitable for a wide range of use cases that involve web application security. It helps protect applications from common web vulnerabilities such as SQL injection, cross-site scripting (XSS), and remote file inclusion, ensuring the safety of your web applications. AWS WAF can also complement AWS Shield in mitigating Distributed Denial of Service (DDoS) attacks by blocking certain types of malicious traffic based on patterns like excessive request rates or geographic location. It is effective in securing APIs, filtering out malicious requests, and reducing exposure to API-based threats, which is especially important for services that expose RESTful APIs through Amazon API Gateway. Additionally, AWS WAF, which aligns with AWS Security Certification best practices, can be used for rate limiting, preventing bot attacks, brute-force login attempts, or abuse of web resources by restricting the number of requests from a single IP address. It also offers geo-blocking features to restrict access based on users’ geographic locations, which is useful if your application should only be accessible from specific countries or regions. Bot mitigation rules can be deployed to reduce the impact of automated bots attempting to scrape your website, brute-force login systems, or carry out spam attacks. Furthermore, AWS WAF aids in compliance with security standards by enforcing web security policies and protecting sensitive data, helping businesses meet regulatory and security compliance requirements. With its flexible configuration options, AWS WAF can be tailored to fit a variety of security needs, allowing organizations to maintain a secure and resilient web infrastructure.
AWS WAF vs Traditional Firewalls
While both AWS WAF and traditional firewalls offer web application security, they differ in several key aspects:
- Application-Level Protection: AWS WAF operates at the application layer (Layer 7), inspecting HTTP and HTTPS requests to identify application-specific attacks such as SQL injection, XSS, and bot traffic. Traditional firewalls often operate at the network layer (Layer 3 or 4) and focus on blocking traffic based on IP address, port, or protocol, offering less granular control over application-level traffic.
- Integration with AWS Ecosystem: AWS WAF is fully integrated with Amazon Web Services (AWS) like CloudFront, ALB, and API Gateway, allowing easy deployment across AWS-hosted applications. Traditional firewalls generally require separate infrastructure and configuration.
- Flexibility and Customization: AWS WAF allows users to create custom security rules and integrates with other AWS services for real-time visibility, logging, and alerting. Traditional firewalls are typically more rigid and require manual intervention to customize rules and monitor traffic.
- Scalability: AWS WAF is a cloud-native solution that scales automatically as traffic grows, while traditional firewalls may require hardware upgrades or manual configuration to handle increasing traffic.
- Managed Service: AWS WAF is a fully managed service that requires minimal maintenance, whereas traditional firewalls often require manual configuration and management of hardware or software.
Configuring AWS WAF Rules
Configuring AWS WAF rules involves defining conditions under which web traffic should be allowed, blocked, or counted. To begin, you need to create a Web ACL (Access Control List), which contains the rules that will filter incoming traffic based on specific criteria. You can either create custom rules or leverage AWS Managed Rules, which are predefined to block common attacks like SQL injection, cross-site scripting (XSS), and more. Rules can be configured to inspect various elements of the request, including IP addresses, HTTP headers, body content, and query string parameters. For each rule, you can set an action, such as allowing, blocking, or counting traffic based on whether it matches the defined conditions. As covered in AWS Training , once your rules are configured, you attach the Web ACL to AWS resources such as Amazon CloudFront distributions, Application Load Balancers (ALBs), or API Gateway to start filtering traffic. Afterward, it’s important to test and adjust your rules to ensure legitimate traffic is not accidentally blocked while effectively filtering malicious requests. Monitoring traffic using AWS CloudWatch allows you to make data-driven adjustments to your rules, ensuring optimal performance and security. This approach helps fine-tune your AWS WAF setup for maximum protection against potential threats.
AWS WAF with AWS Shield and AWS Firewall Manager
AWS WAF can be used with other AWS services, such as AWS Shield and AWS Firewall Manager, to enhance the security posture of your web applications.
- AWS Shield: AWS Shield is a managed DDoS protection service that helps protect AWS applications from large-scale attacks. While AWS Shield protects against volumetric and state-exhaustion DDoS attacks, AWS WAF focuses on filtering malicious web traffic at the application layer. The two services complement each other for comprehensive protection.
- AWS Firewall Manager: AWS Firewall Manager simplifies the management of AWS WAF rules across multiple accounts. This is especially useful for organizations with multiple AWS accounts or complex network architectures. AWS Firewall Manager helps enforce consistent security policies across all applications by automating the deployment of WAF rules.
- Protection from Web Exploits: AWS WAF helps protect web applications from common vulnerabilities, such as SQL injection, cross-site scripting (XSS), and other OWASP Top 10 threats.
- Enhanced Control: AWS WAF allows you to create custom security rules and use managed rule sets, giving you fine-grained control over what traffic is allowed or blocked.
- Bot Mitigation: AWS WAF’s bot control features help identify and mitigate malicious automated traffic, protecting your application from bots performing credential stuffing, content scraping, and other malicious actions.
- Automatic Scaling: AWS WAF automatically scales with your traffic volume, ensuring it can handle significant traffic and growing security requirements without manual intervention.
- Review and Test Rules Regularly: Monitor your traffic and adjust your WAF rules to ensure optimal protection while minimizing false positives.
- Use Rate Limiting: Protect against brute-force attacks and DoS attacks by configuring Rate Limiting based on IP addresses.
- Leverage Logging and Monitoring: Enable detailed logging and monitor AWS WAF metrics through Amazon Cloudwatch to stay aware of security incidents and fine-tune your protection.
- Integrate with AWS Shield: Use AWS WAF with AWS Shield for comprehensive protection against application and network-layer DDoS attacks.
Excited to Obtaining Your AWS Certificate? View The AWS Training Offered By ACTE Right Now!
Logging and Monitoring with AWS WAF
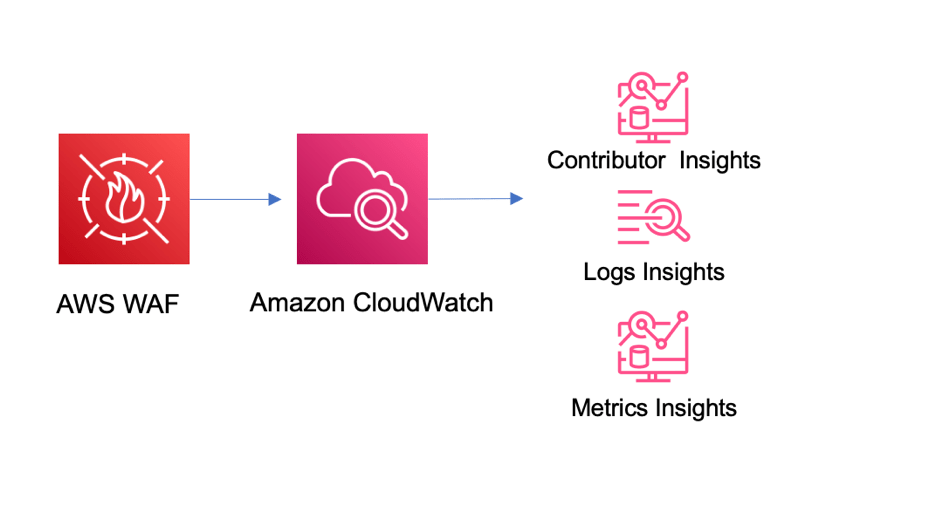
AWS WAF provides detailed logging and monitoring capabilities through integration with Amazon CloudWatch and AWS CloudTrail, allowing you to gain valuable insights into web traffic and security events. Through CloudWatch Metrics, AWS WAF generates metrics that track the number of allowed, blocked, and counted requests. These metrics are essential for identifying potential security threats and fine-tuning your rules to improve protection. Additionally, CloudWatch Logs can be configured to receive logs for a deeper analysis of web requests, enabling you to examine attack trends, evaluate the effectiveness of existing rules, and identify any potential vulnerabilities. AWS CloudTrail further enhances monitoring by logging AWS WAF events, providing an audit trail of who created, modified, or deleted rules. This integration ensures that you can track every action made in your AWS WAF configuration, enhancing accountability and helping with compliance and troubleshooting. With these combined tools and AWS Global Accelerator, AWS WAF provides robust visibility and monitoring capabilities to support continuous security improvements.
Security Benefits of AWS WAF
Are You Considering Pursuing a AWS Master’s Degree? Enroll For AWS Master Course Today!
AWS WAF Pricing Model
AWS WAF pricing is determined by several factors, including the number of web access control lists (Web ACLs) you create, the number of rules within each Web ACL, and the volume of requests processed by the service. You are charged for each Web ACL you create, as well as for each rule you configure within the Web ACL. Additionally, AWS WAF incurs charges based on the number of web requests it processes, with higher traffic resulting in higher costs. For those using AWS Managed Rules, there is an additional charge based on the number of managed rules you subscribe to. To help you better manage your costs, AWS provides a cost calculator that estimates expenses based on your specific usage patterns, allowing you to predict and optimize your spending. This pricing structure is designed to be flexible, enabling you to scale your security protections according to your needs without incurring unnecessary costs.
Best Practices for AWS WAF Implementation
Start with Managed Rules: Begin using AWS Managed Rules to quickly protect against common threats and then fine-tune with custom rules.
Preparing for AWS Job Interview? Check Out Our Blog on AWS Interview Questions & Answer
Conclusion
AWS WAF is a powerful and flexible tool for protecting web applications against security threats. AWS WAF provides a robust solution for safeguarding web applications with its custom rule creation, real-time traffic monitoring, and integration with AWS services like AWS Shield and AWS Firewall Manager. By leveraging the built-in security features and following best practices for rule management, AWS WAF helps organizations maintain a secure and compliant web environment while minimizing the impact of malicious traffic. AWS Training also enhances operational efficiency by automating security rule deployment and adapting to evolving threats. Additionally, AWS WAF offers advanced features like bot mitigation, rate limiting, and geographic blocking, providing comprehensive protection. With its scalability and ease of integration, AWS WAF is an essential tool for businesses looking to strengthen their web application security.





